DevSecCon Singapore 2018
14 Talks
Recorded in February 2018
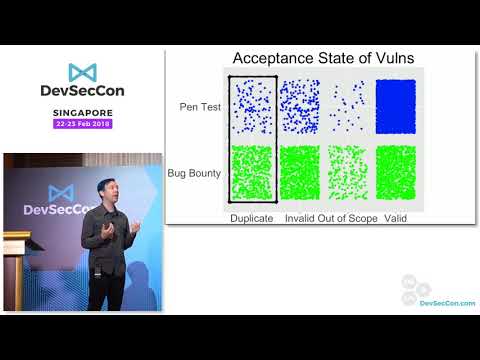
Closing Keynote: Measuring and maximizing vuln discovery efforts
Closing Keynote: Measuring and maximizing vuln discovery efforts
In graph we trust: Microservices, GraphQL and security challenges
In graph we trust: Microservices, GraphQL and security challenges
Opening Keynote: Lessons learned defending web applications in the age of DevOps/Cloud
Opening Keynote: Lessons learned defending web applications in the age of DevOps/Cloud
Securing automation and solving the Secret Zero problem.
Securing automation and solving the Secret Zero problem.
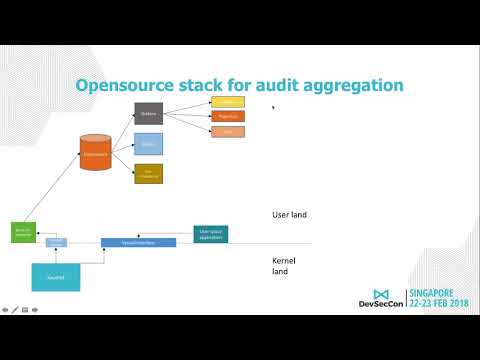
System call auditing made effective with machine learning and selective reporting
System call auditing made effective with machine learning and selective reporting